Another post from series B2B (Back2Basics) is related to the Apple Business Manager (ABM). This time I will write something about Federated Authentication in ABM.
What is Federated Authentication? You can read a bit about this on Wikipedia. I want to directly focus on the knowledge how to configure it.
First, you need to have configured verified domain – and the process I’ve described it on this post: B2B – ABM – Adding own domain!
If that prerequisite is filled, you can go to the next step – and configure this authentication.
Requirements for Microsoft is that you need to have one of enabled role:
- Global Administrator
- Application Administrator
- Cloud Application Administrator
In my case, I will use account with the one of the lower permission – Cloud Application Permission.
The main difference between Cloud Application Administrator and Application Administrator is that the first one cannot use Application Proxy in Entra.
Me 🙂
Now you can go to the ABM > Organization on left bottom > Preferences > Accounts > Federated Authentication > Click Edit button and Select Microsoft Azure AD (heheh, that should be Microsoft Entra ID ;))
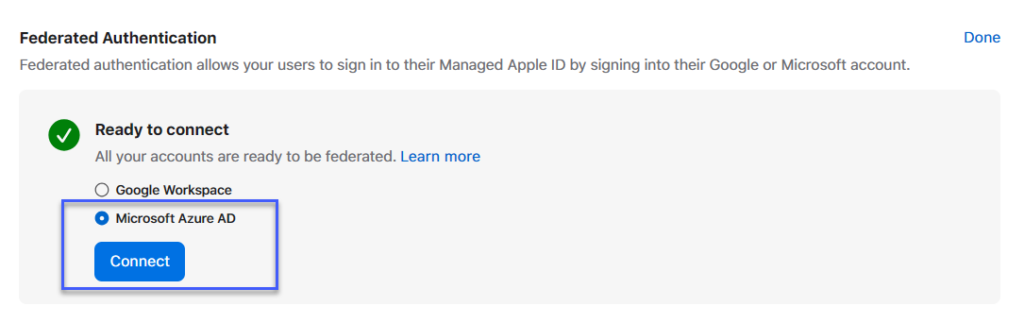
Click Sign in with Microsoft and logon using proper account with necessary permissions.
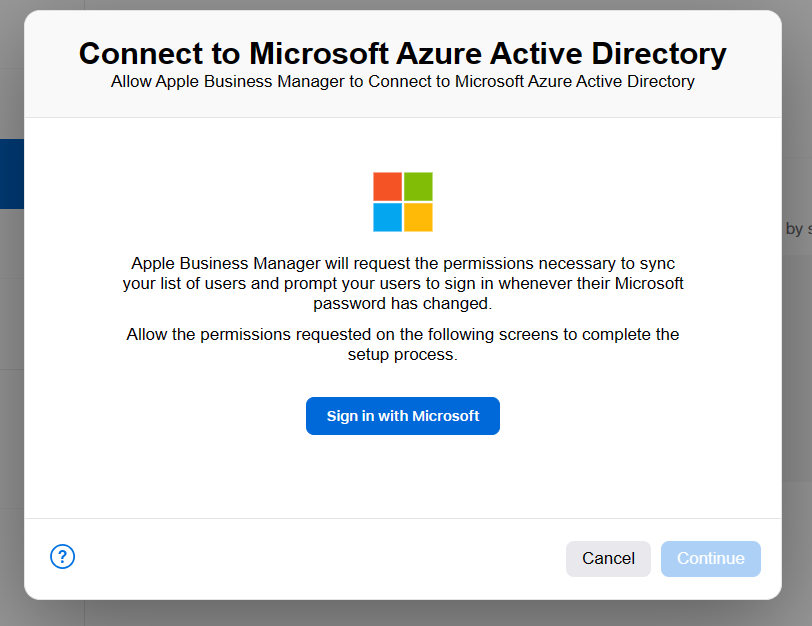
Approve necessary permissions:
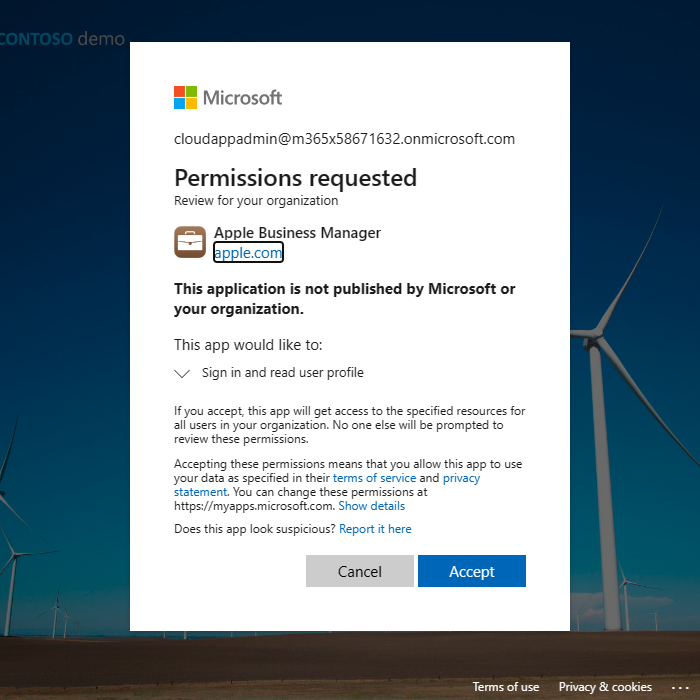
And you should see the window that Federated Authentication Setup Complete.
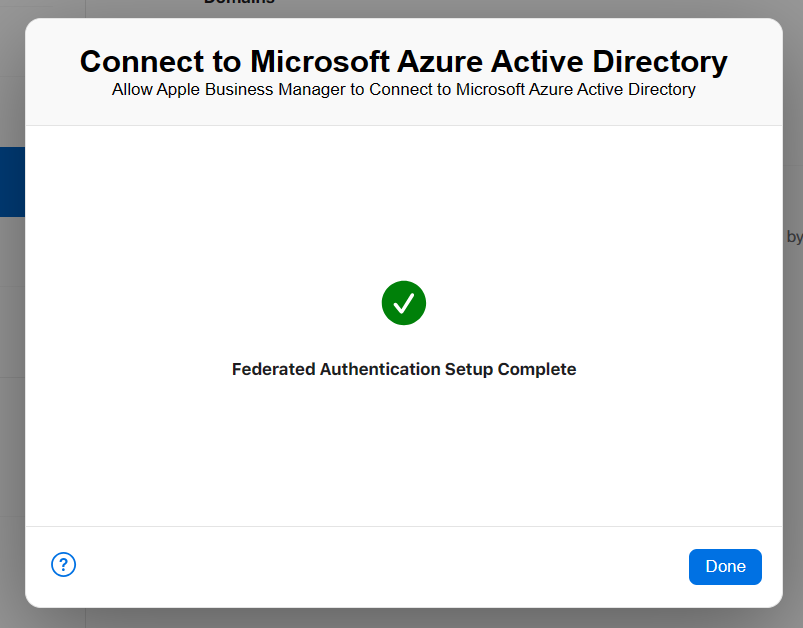
Finally, option in Accounts tab should looks like:
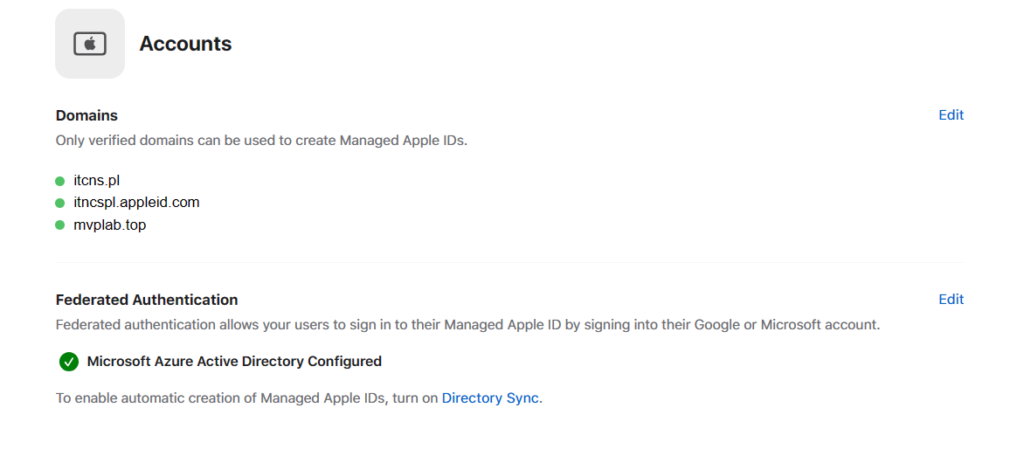
And for this post – it is everything. On the next post I will show you how to start usage of Directory Sync to have all, required accounts from Microsoft in ABM.
Stay tuned!
You can check all entries from B2B series on this link.


