Last time I spend very long time for configuring Microsoft Tunnel… About this solution will be post shortly, but.. Now I want to share some knowledge with you how to deal with one of requirements for that solution – the TLS certificate. Wasn’t easy to generate it, because for most of blog posts or documentation – there are no exactly information how to generate it and what are possible solution for people without internal – corporate PKI.
So I decided to show you how to generate Free Let’s encrypt certificate for Microsoft Tunnel solution. Or any other solution. 🙂
So, let’s start!
First, you need to have installed proper module – it’s named Posh-ACME,
You can do that using command:
Install-Module -Name Posh-ACMEAfter installation, you can start generating required certificates.
I will provide example command to generate certificate:
New-PACertificate mstunnel.msmvplab.top -AcceptTOS -Contact [email protected] -DnsPlugin AcmeDns -PluginArgs @{ACMEServer='auth.acme-dns.io'} -Install -PreferredChain 'ISRG Root X1'Where on the first parameter is domain name, you can use wildcard, on my case I’m generating certificate for subdomain.
Second parameter is for automatic agree for terms of use.
Contact – I think there is nothing to add
Fourth is more interesting, because you need to select what method do you want to check ownership of your domain. Full list of “plugins” are visible on this link. And the next one – is related to the parameters to use with that ‘plugin’ – more information about those two parameters are here
Install parameter – if will be set, certificate will be automatically placed on the Cert Store for Device > Personal.
And.. The last one. The most important for my lab – PrefferedChain. I needed to set up this parameter, because for the Microsoft Tunnel was requirement to deliver whole chain of Certificate – starting from Root Certificate. That was a reason, why generating certificate without this parameter – wasn’t working properly and I was getting the information that you need to provide a cert with whole chain during installation.
When you execute that command, you need to provide an ownership of your domain.
In my case, I got a request to create a new CNAME record:
Please create the following CNAME records:
------------------------------------------
_acme-challenge.mstunnel.msmvplab.top -> 442cf589-4dcb-4b0c-8911-a346b118e61c.auth.acme-dns.io
-----------------------------------------When record will be created and visible for our plugin provider, certificate will be generated and stored (or exported only) in our device.
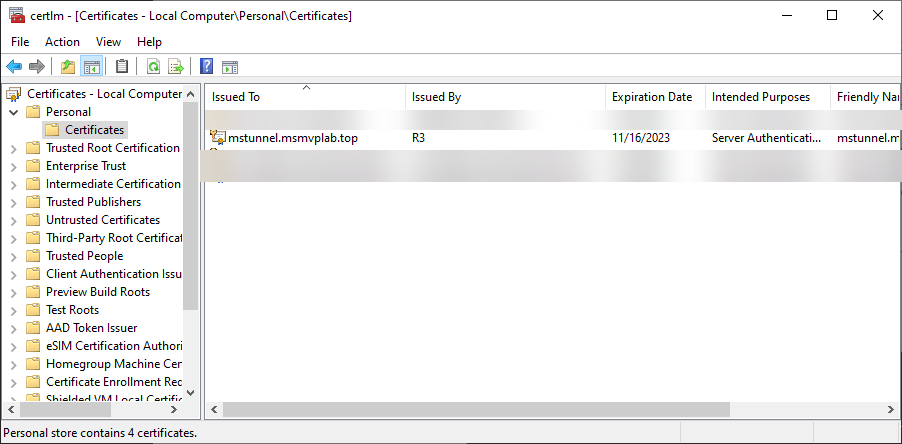
Of course, you can export this certificate from here with password:
poshacme
Or take it from your %LOCALAPPDATA%\Posh-ACME folder.
Of course – you can also specify the password for this certificate using -PfxPass or -PfxPassSecure parameter.
And.. For the MS Tunnel I needed to copy fullchain.pfx to my Linux machine.
If you want to renew that certificate – use command:
Submit-RenewalOf course, you can create a scheduled task for some kind of automation. Also, what is important – you need to create some task for coping the pfx file to machine with MS Tunnel docker image and reload this cert.
Have fun!


