Are you working on the IT Support and you’re bored with procedures of temporary passwords for new joiners or for users who didn’t remember their passwords?
I was working on IT Support for many years. Yes, I know how looks the procedures for the new-joiners are related to the first password. I also know how looks the procedures for people, who didn’t remember their passwords.
In many cases, you need to reset it on Active Directory, send one part of the password to the end-user, the second part to the manager/director, etc… But what if you can use a dedicated Azure AD function named Temporary Access Pass for that kind of case?
For example, you can generate the password with a length of 10 characters, which can be the maximum available for the user for one next hour and can be used only one time?
I see many examples to use that tool, but most of them – onboarding new-joiners who didn’t have configured Self Service Password Reset.
Let’s start!
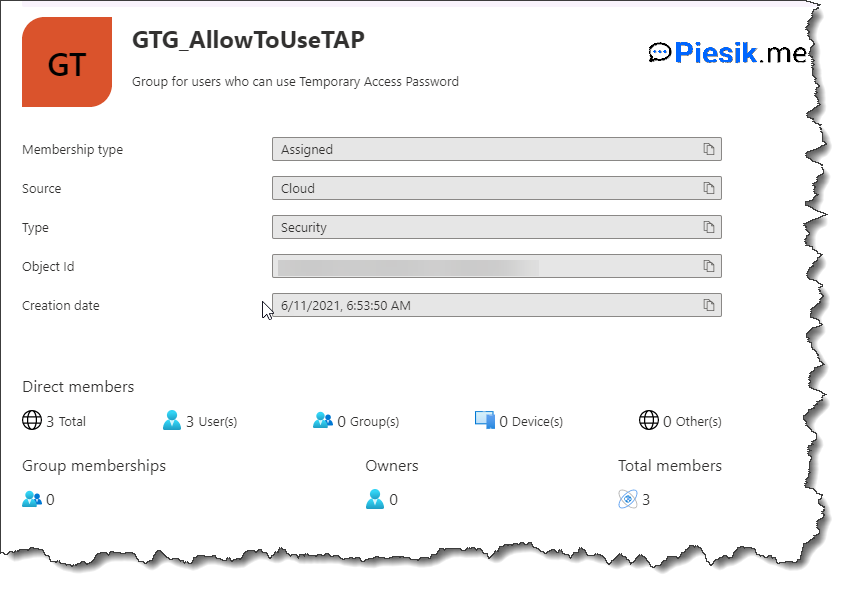
In my case, I created a new AD group where I will have all users who can use that feature. Of course, you can use it for all users, which is selected by default, by you should first test this feature on a small group of users. It is a recommended behavior.
The second step is to open the Azure AD portal > Security > Authentication methods > Temporary Access Pass and enable it from the left side.
In the middle, you need to select a proper group(s) to which you want to assign the TAP policy.
On the right side, you need to configure options about policy for TAP. Let’s see how I configured policy:
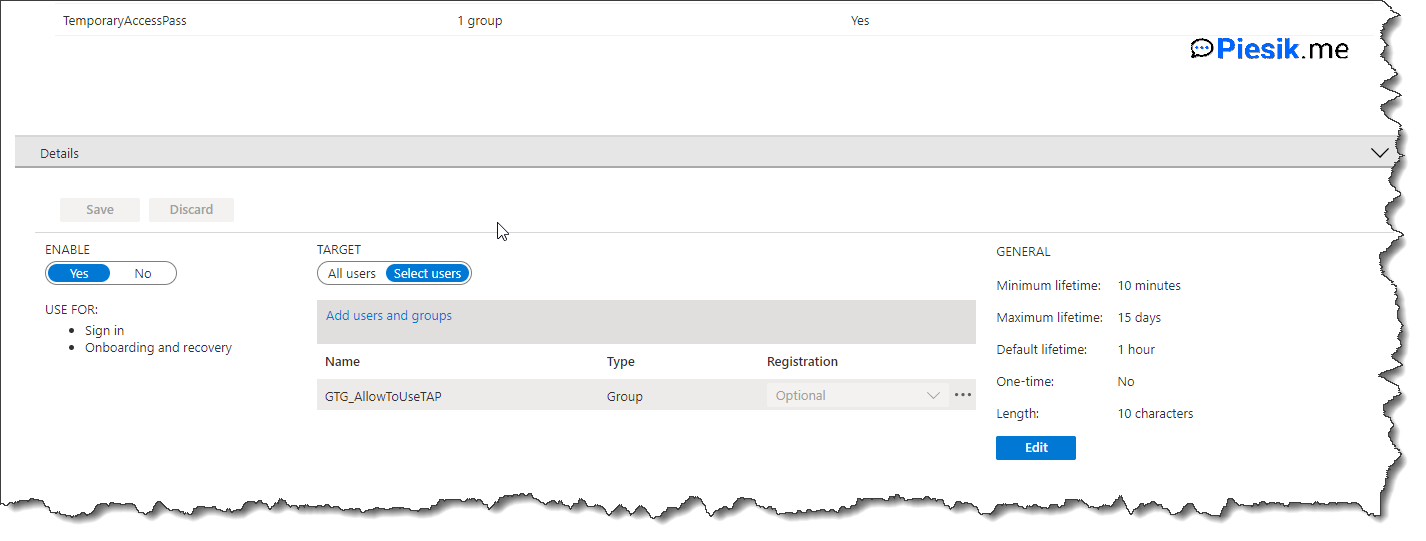
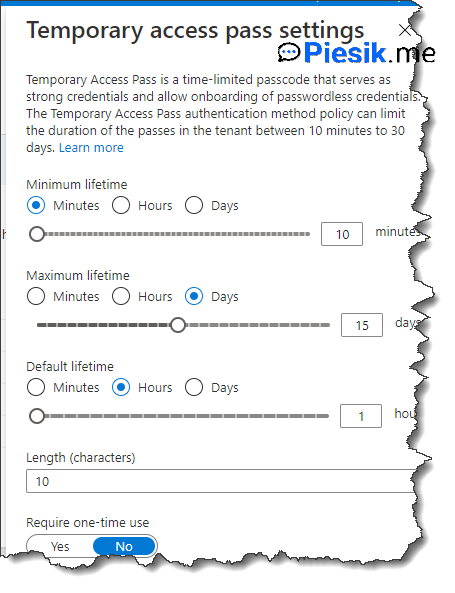
The minimum life of a password is 10 minutes, but the default lifetime is 1 hour. The maximum time is 15 days and can be used multiple times. Also – the length is 10 characters.
But you can configure those settings differently. More information below:
Ok, so let’s provide a temporary password for Diego Siciliani!
To do that, open AAD portal > Users > Authentication methods and enable the new Authentication methods experience.
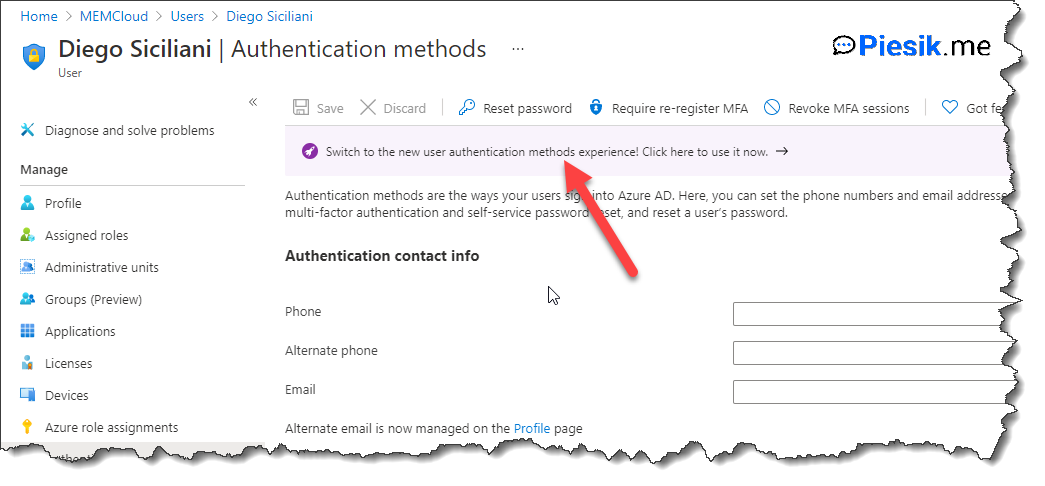
After that, click on the Add Authentication method button, select TAP and provide necessary details. You can set a delayed start time if you know for example – this user needs to go back from home to the office etc…
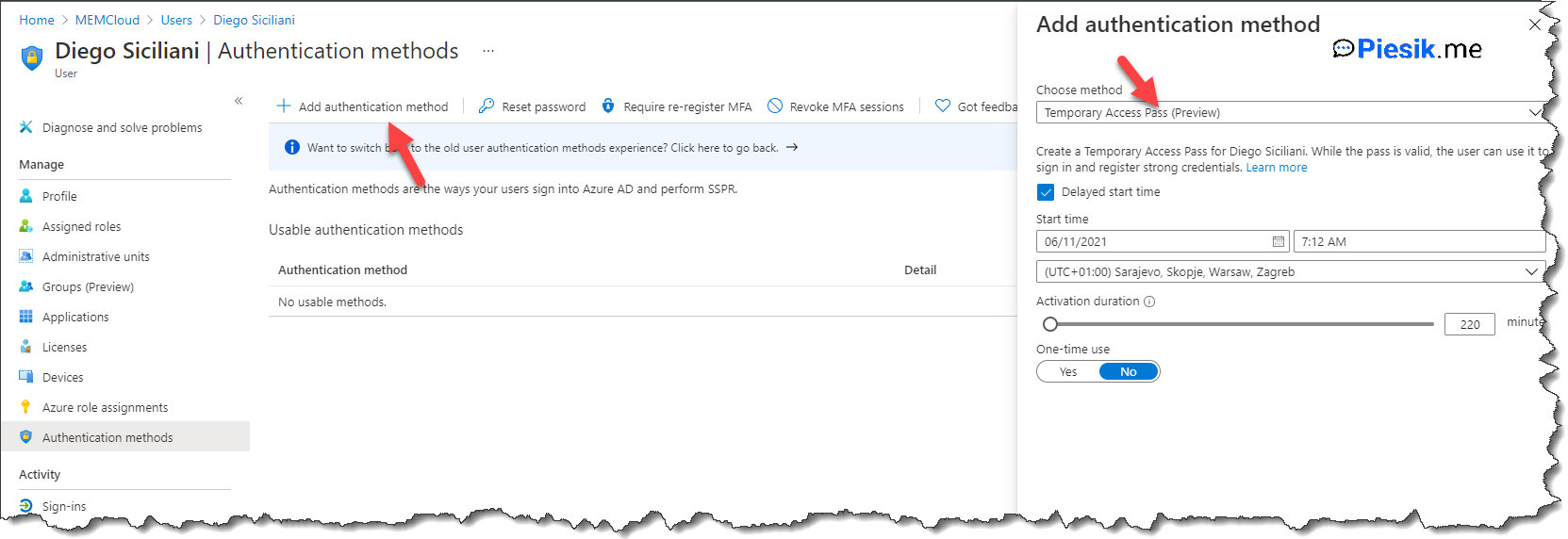
When you generate the password, there will be not possible to read it again so, copy it to your notepad and provide the user.
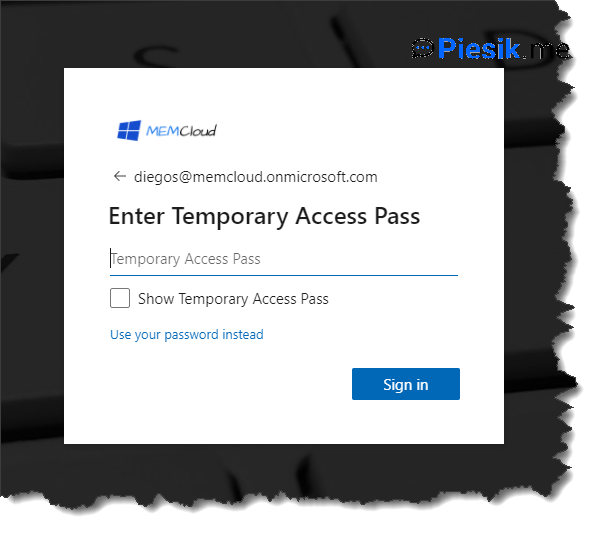
End-user needs to open the https://aka.ms/mysecurityinfo page, provide own UPN, and by default need to provide TAP to login and change password to own.
What with roles and possibilities to use TAP in Azure AD?
Docs says:
Global administrator can create, delete, view a Temporary Access Pass on any user (except themselves)
Privileged Authentication administrators can create, delete, view a Temporary Access Pass on admins and members (except themselves)
Authentication administrators can create, delete, view a Temporary Access Pass on members (except themselves)
Global Administrator can view the Temporary Access Pass details on the user (without reading the code itself).
I think this option looks very interesting, especially for onboarding users.

